As the tech world continues to gravitate toward digital modernization, cloud-based platforms, and consistently updated applications, businesses of all shapes and sizes need to take a modern approach to sharing data. A modern approach to data sharing includes accounting for the ever-evolving landscape of data security and the technology that makes it possible.
Overall, it should be straightforward for people to share data in a way that boasts security and efficiency, and cloud applications are bringing that idea to life. Sharing data externally is proving to be highly beneficial from a financial standpoint.
The Modernization of Company Technology
Most companies understand that successfully competing in a digital age demands flexible and scalable IT systems. Experimenting with data sharing and the applications or cloud platforms that work best for your business is expected and allows for quick changes that won’t derail projects and workflows.
As a result of this experimentation, businesses on a global scale began to launch programs that focus on modernizing their technology and legacy systems, concentrating on rethinking the modernization process and how they should go about it. A vital component to digitally transforming a business is realizing the potential impact of sharing data in real-time. Real-time sharing of data and analytics is crucial to the modern approach to utilizing data insights.
Relying only on internal data is no longer sufficient. However, if companies can make the correct data information available to the right people, collaborations begin to form, and valuable insights and knowledgeable input can improve business decision-making.
Modernizing company technology can have an incredible impact on many industries where data in real-time is crucial to quality assurance, including food sourcing, customer experience, aviation safety, and efficient global supply chains. There isn’t an industry on Earth that won’t see improvements from sharing data in real-time because it enhances the ability to make educated decisions faster.
Improving How We Share Data
Several ways exist to improve how companies share their data with trusted sources. Blockchain technology, for example, is a distributed database that enforces secure and tamper-proof transactions. It’s a valuable tool for securely sharing data without bringing in a third party’s services.
Businesses could also consider improving their data-sharing capabilities through the use of the cloud, a prevalent way for most companies to modernize the way they share data without completely breaking down the current systems they have in place. Cloud storage creates an avenue for organizations to share and store large amounts of data and files without worrying about the amount of available storage space or limitations to the bandwidth.
With cloud storage, you can access business data from anywhere as long as you have approved login information. With the surge of remote workers and hybrid work environments across the globe, businesses have taken to operating on cloud platforms and updating their current systems to improve how their employees can log into work servers. It’s also easy to track logins, adding another layer of safety to the data-sharing strategy.
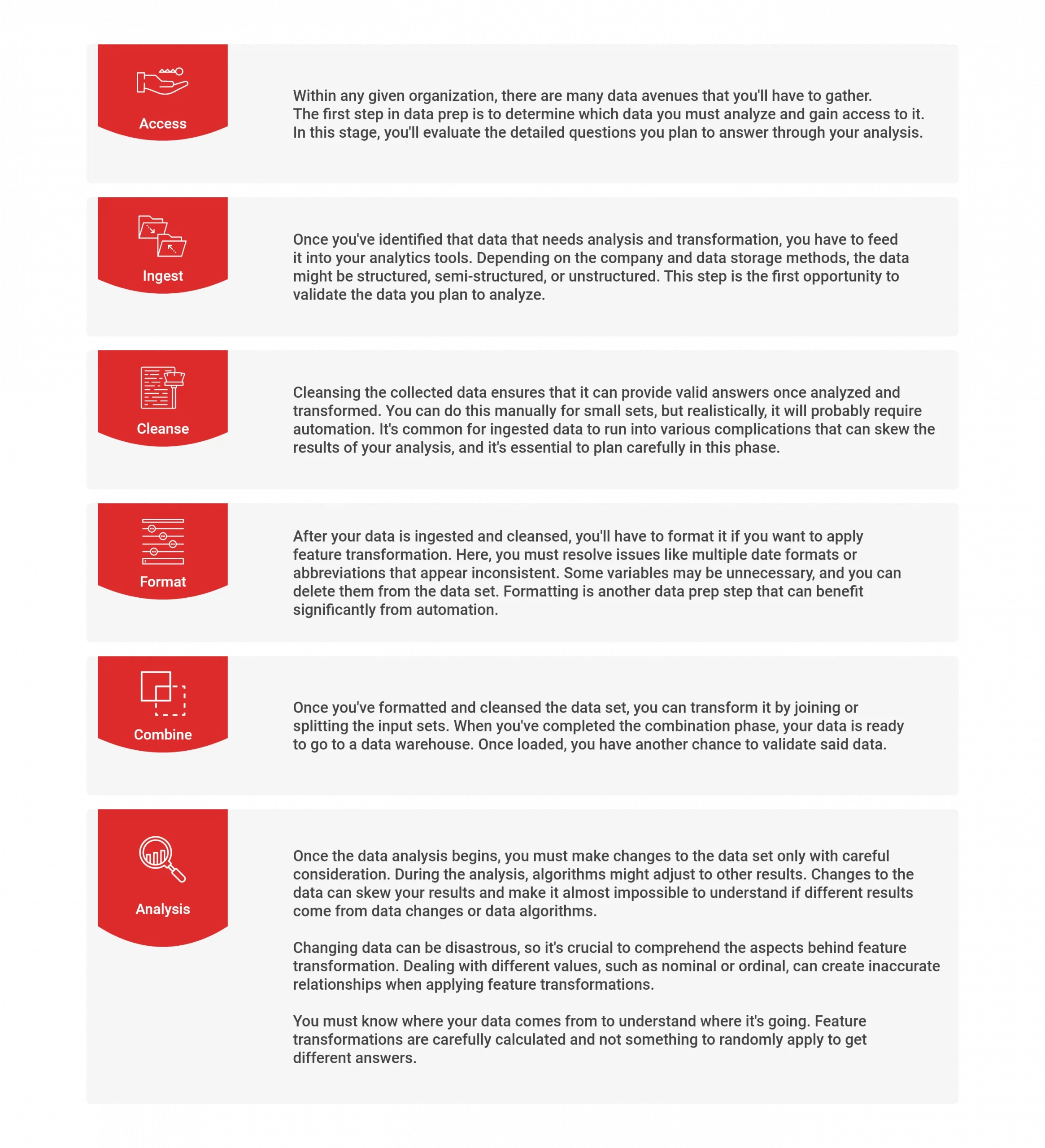
The data-sharing process has to begin somewhere, and instead of discussing the challenges that process can bring, we’ll focus on how to improve our understanding. To modernize the ways in which we share data, we must first grasp the importance of the API, fully comprehending the API journey.

Understanding the API Journey
Everyone has probably come across the acronym “API” at some point in their business journey, primarily if they have an online presence. API stands for application programming interfaces, and they’ve become a vital component of modernizing digitally for most businesses. APIs allow companies to link data and systems, playing a massive role in responsiveness and adaptability.
Still, it takes skill and expertise to implement APIs properly, and things can get messy when done incorrectly. When APIs are poorly executed, companies will find redundancies and limited transparency, adding confusion instead of clarity to how we share data. It’s crucial not to get caught up in wasting time rebuilding and replacing legacy systems by adding APIs without a plan, causing regression rather than progression.
Instead, understanding the API journey begins with defining the APIs our businesses need to build, fully comprehending which data needs real-time access and which employees and team members (and sometimes third parties) need access to that data. APIs are the bridge between the various systems that provide access to information.
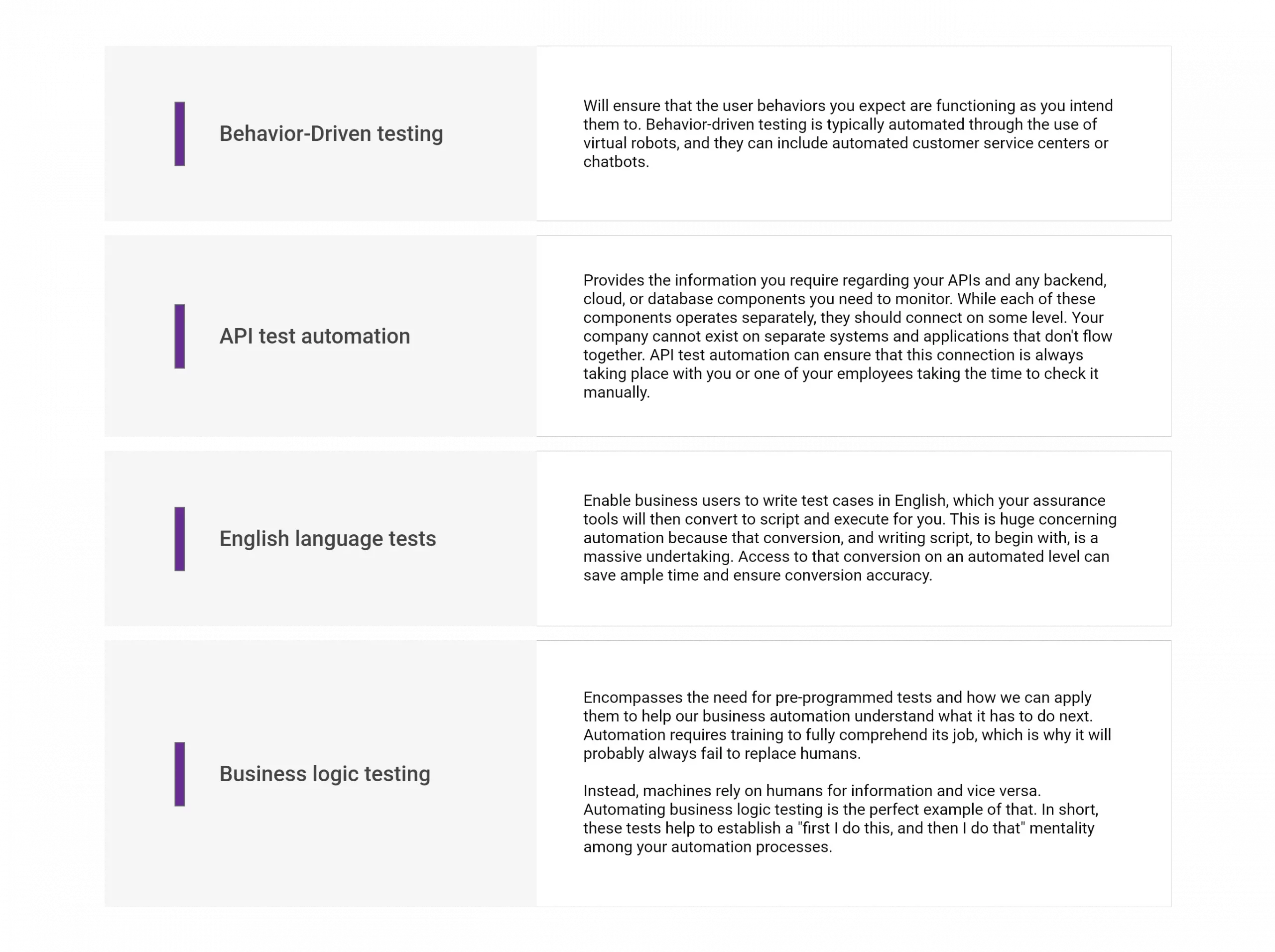
APIs are relatively flexible, so choosing which ones to build can be overwhelming, with API tests taking up more time than you’d prefer. You must begin with enabling solutions that will provide your company with a solid technical foundation while improving your customers’ journey. Develop your APIs based on the goals you have for your business and how you intend to modernize those goals.
A great example is a traditional bank competing with a technologically advanced fintech by building an API that enhances its customer experience. Introduce efficiency to your consumer base through API architecture wherever possible.
Managing APIs
Building APIs and successfully managing them are two very different things. If a company has a large number of APIs, a solution to manage said APIs makes sense. API management is a way to centralize your APIs, simultaneously keeping your services secure while sharing necessary documentation and data.
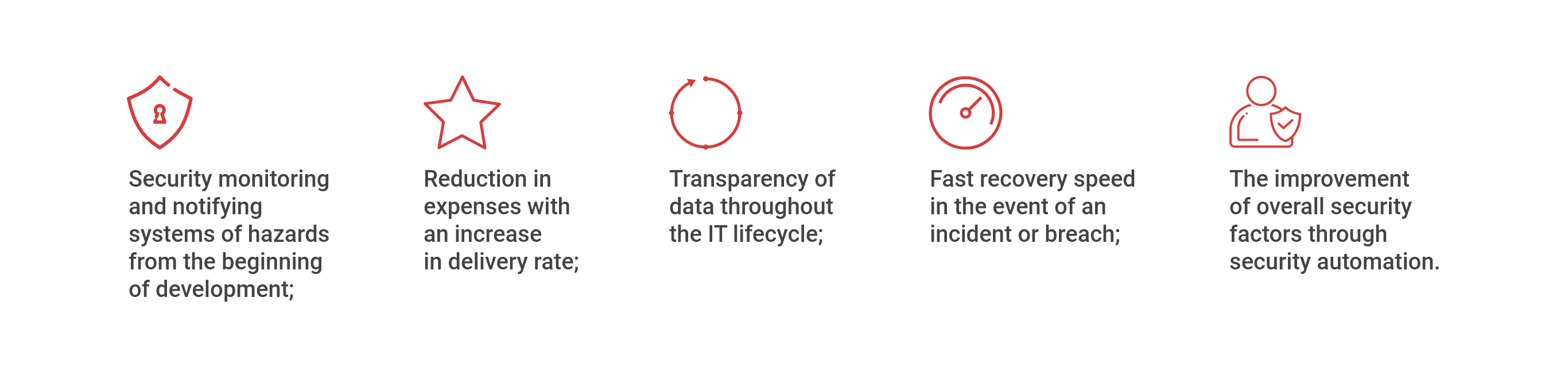
Managing your APIs should include a gateway, developer portal, and analytics dashboard for consistent real-time monitoring. API management solutions can help you keep track of your website traffic, connections, security measures, and errors. An API management solution can be tricky to implement, and you must consider additional security layers for exposed systems, rigid access control regulations, lifecycle management, and maintenance.
Properly building APIs and employing them at their full potential is a long road full of challenges. The orchestration and security implementations alone can be time-consuming and frustrating, and onboarding and integrating new partners and systems doesn’t help alleviate the stress of enforcing a new API architecture.
Sharing data in real-time means growing your partner network, which comes with a load of technical work to function so that you can begin to recognize the value of the data presented. APIs are a fantastic data-sharing approach but don’t come without risk, effort, and extensive costs. It’s not uncommon for many businesses, primarily those short on time and funding, to struggle with constructing and working with API IT systems.
A Modern Twist on Traditional APIs
Most businesses today are driven by data, and many have begun to rethink the API approach to sharing said data. Overall, the API approach needs an upgrade to ensure data consistency, especially when various data sources are involved.
Earlier in this article, we mentioned cloud-based data sharing (a standard and typically fast replacement for legacy systems), but we also touched on the concept of blockchain technology. Blockchain technology is dripping with potential, but business leaders must recognize its limits when scaling storage, bandwidth, and power computing. However, connecting blockchain technology to cloud infrastructure could be the modern solution to a technology that would raise the bar for data sharing if it were serverless.
Serverless functions take away the complications within infrastructures that blockchain technologies typically present. Serverless functions provide the perfect solution for unlimited (but costly) computing resources, with no single infrastructure management necessary. With serverless functions, you can scale down resources when they’re not in use, making them on-demand and, therefore, more convenient than they’ve ever been before.
The combination of Blockchain and serverless technology presents a myriad of powerful capabilities. It’s essentially a way to scale data and provide business leaders with a solution entirely native to the cloud, employing desirable aspects like unlimited storage and never-ending networking capabilities.
Scalability and flexibility are must-haves concerning solutions that assist companies in data sharing. Flexible solutions allow storing data from different sources without creating competition for resources. It’s revolutionary.
The combination of serverless and cloud technology provides an innovative answer for companies that want to share data through various organizations. It presents the ability to focus on building applications driven by value and consumer preferences, demands, and expectations.
Business network participants could share data externally, with plenty of access control, in real-time. The number of doors this opportunity opens up is endless, and there is no need to dedicate precious resources to resolving and managing the consistent string of problems that comes with the (often incorrect) building of API architecture
Sharing Data from a Modern Perspective
The modern implementation of data-sharing solutions should be time-consuming. Modernizing technology was once an endeavor that took business leaders years to achieve, but collectively, we’re not there anymore. To modernize successfully, look to the tools that can help your business advance, share data externally and safely, and explore the full potential you have to create a partner ecosystem that works for you.
The idea of digital modernization is to get there faster but also in an efficient manner. Building the API architectures of yesterday is looking more and more like the modernization of the past with each passing day. However, combining serverless and Blockchain technology is the modern approach to data sharing that we’ve all been waiting for.

















Recent Comments